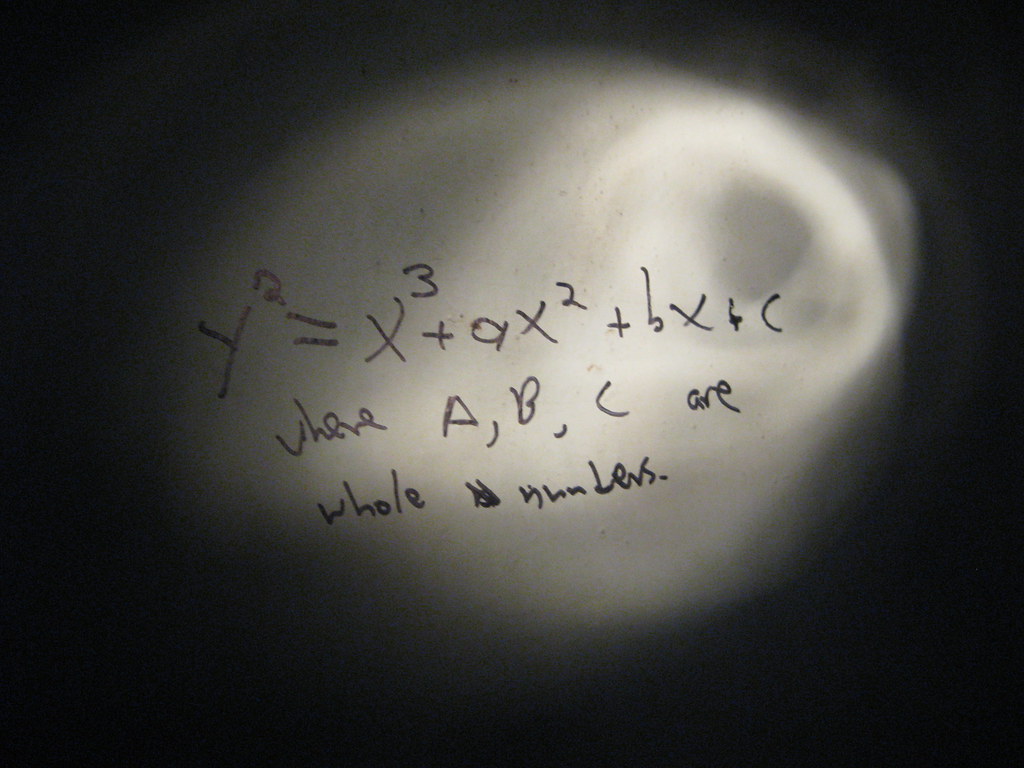Blog Posts
Elliptic Curve Cryptography
Let $y^2 = x^3 + ax + b$ be the equation of the elliptic curve E. Any line L that intersects the curve will intersect the curve in at most 3 points. Below are examples of how these lo...
In Cryptography, Feb 27, 2018Quantum Searching
Imagine a shuffled deck of 52 cards, and you are asked to find the ace of spades. The most natural thing to do is to take the top most card, see if it’s the ace of spades. If not, put...
In Searching, Nov 06, 2017RSA Encryption and Quantum Computing
We are going to crack the RSA by finding the period of the ciphertext. Let m be the message, c the ciphertext, e the encoding number and N=pq such that
In Cryptography, Oct 15, 2017Period Finding and the RSA
In the previous post, we learned how to decrypt RSA by getting the factors of the big number N and computing for the inverse of e (the encoding number) modulo N. There is also another...
In Cryptography, Oct 15, 2017How RSA Encryption Works
Alice and Bob live in different parts of the world. They want to communicate with each other but they don’t want anyone to know the messages they exchange. In order to protect the mes...
In Cryptography, Oct 15, 2017Introducing Quantum Computing
As I watched my one-month old baby sleeping, a thought ran through my mind. I wonder what technology would look like when she’s my age. There’s a lot of things going on simultaneously...
In Quantum Computing, Sep 15, 2017